Network Security Monitoring
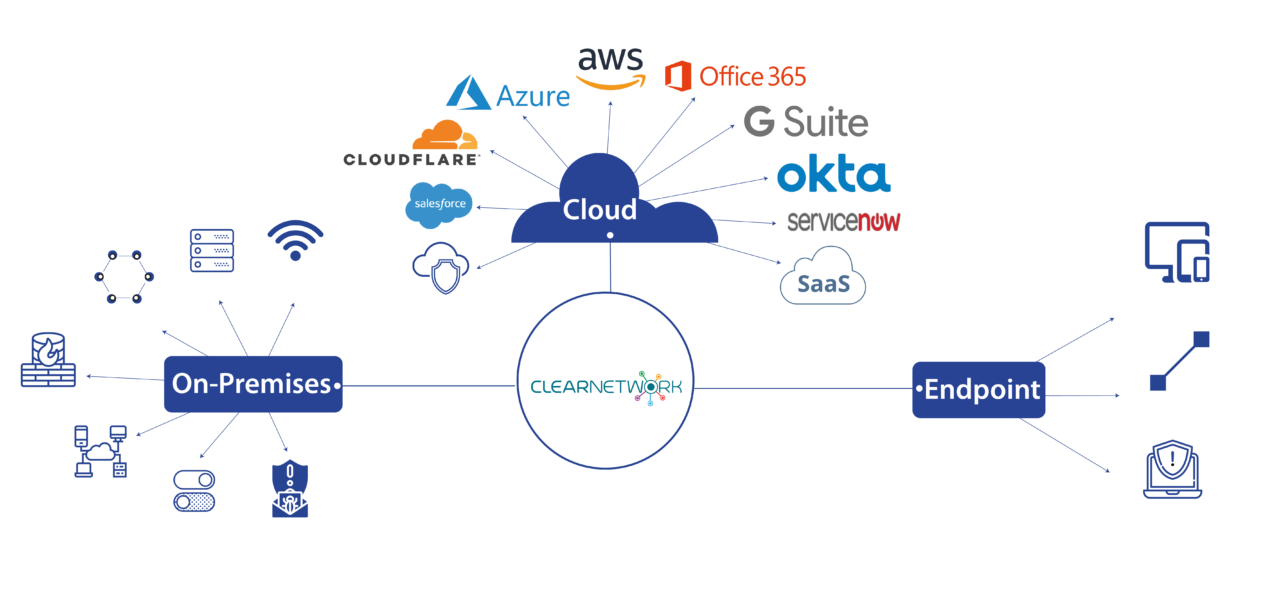
Our Network Security Monitoring provides 24/7/365 threat monitoring, alerting, validation and proactive threat hunting. We manage a suite of best-in-class security technologies, with the best threat intelligence. The result is that we discover threats in your network, endpoints, cloud and applications that your other systems miss. We can even disable networking on infected devices, stopping the attack before it spreads and giving your IT team more time to remediate. We help you be proactive as well, with asset discovery and vulnerability assessments that show you where you’re vulnerable.
200+
99%
Customer Retention Rate
20+
Years in business
Detect and Respond to Cyberthreats Before they Impact your business
SIEM and Log Management
Using SIEM and Log Management, our security analysts continuously monitor your network, endpoints and cloud using the best threat intelligence and machine learning.
Auto-Containment
Asset Discovery, Vulnerability Management and industry leading threat intelligence show you where you’re at risk. With this data we help you be proactive to reduce risk, and determine what assets in your network and cloud are most vulnerable.
Continuous Monitoring
Expert security analysts in our US based Security Operations Center (SOC) are assigned to your network and monitor your network, cloud and endpoints for threats and work with you to quickly resolve them.
Threat Intelligence Feeds
We use the latest threat intelligence from multiple feeds to keep your network secure against
Threat Hunting
Our expert security analysts search deep for hidden threats in your infrastructure that threat intelligence has not yet discovered.