Many organizations take a reactive approach to cybersecurity. Often, the first indication that they have that something is happening on their network is when they receive an alert of an attack in progress.
However, by this point, it may already be too late to stop the attack. Cyber threat actors are becoming increasingly sophisticated, and many of them can remain undetected until they achieve their objective on their target. An example of this is ransomware, where the malware stealthily infiltrates a machine and only announces its presence when it has finished encrypting the user’s files.
By taking a proactive approach to security, security teams can identify infections while they are still in the “stealth” phase, allowing them to be remediated before they do significant damage to the organization. To do this, the security team needs to learn to threat hunt.
What is Threat Hunting?
Threat hunting is the practice of proactively going after cyber threats rather than waiting for an alert to start investigation and remediation. The more quickly that a threat is identified and remediated in the cyberattack lifecycle, the less damage that it can do to the organization.
A proactive approach like threat hunting is often more difficult than a purely reactive cybersecurity strategy. An alert-driven security team always knows where to look for potential threats since they have already triggered alarms and have revealed their presence within the network. With threat hunting, the security team has no idea if an attacker currently is present on their network, and, if they are, what they are doing or where to look. Threat hunting requires systematically identifying and testing potential attack scenarios in the hope of catching an intrusion before it is able to do damage.
Why Threat Hunt?
The difficulty of threat hunting may put off many security teams. Doing it right requires a knowledgeable security team supported by the right tools and access to the right data. Putting this together can be difficult; however, a good threat hunt provides several advantages:
- Proactive: With threat hunting, it is possible to identify and remediate a potential threat early in the attack lifecycle. This decreases the ability of the attacker to do damage or steal sensitive data. As a result, a successful threat hunt could save an organization millions in avoided data breach costs.
- Retrospective: Ideally, an organization’s cybersecurity deployment will identify every successful intrusion on the network. In reality, the increased sophistication of cyber threat actors means that some attacks will slip by unnoticed. By performing threat hunts on historical data, it is possible to identify previously-missed intrusions and take appropriate action.
- Wide field of view: An alert-driven incident response strategy is limited to the data available in security alerts. With threat hunting, a security team can investigate potential threats that may not be detectable using the data available in alerts.
Threat hunting has significant benefits but can also be difficult to perform effectively. Before starting threat hunting, it is important to evaluate whether your organization’s security team has the ability to threat hunt effectively. If this is not the case and if threat hunting would be of value to your organization, then looking for a third-party provider may be necessary.
How to Threat Hunt
Threat hunting is based off of the scientific method. To perform a threat hunt, all that a threat hunter has to do is evaluate and test a hypothesis. The main challenge in threat hunting is developing hypotheses that are easily testable and that, once tested, provide useful information.
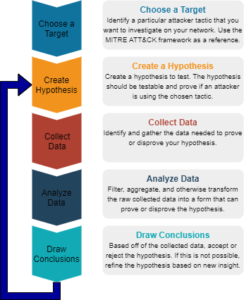
As shown in the image above, threat hunting can be broken into five main stages:
Choose a target
This stage of the threat hunting process is intended to determine the question that the threat hunt is designed to answer. A good resource for making this decision is the MITRE ATT&CK framework, which describes the phases of a cyber attack and various methods that an attacker can use to accomplish each phase. Selecting one of these tactics and trying to detect it on the network is a good starting point for a threat hunt.
Create a hypothesis
In this stage, the threat hunter creates a testable hypothesis that will help to determine if the chosen tactic is being used on the network. These hypotheses should look something like: If X is happening on the network, then it means that <chosen technique> is happening. The MITRE ATT&CK matrix is valuable for this as well since it describes a variety of detection mechanisms for each technique.
Collect data
At this point, the threat hunter collects data designed to determine the validity of the hypothesis. The collected data should be able to point to whether or not X is occurring on the network.
Analyze data
Most data collected during a threat hunt will likely come in the form of one or more datasets with a large amount of noise. In this stage, the threat hunter sifts through and aggregates the data to find an answer to whether or not X is occurring on the network.
Draw conclusions
Based upon the data collected, it should be possible to prove or disprove the hypothesis and take remediative action if the hypothesis is supported. If the collected data does not answer the question, then the hypothesis can be refined based off of the results in order to provide a more useful answer.
Impacts of Threat Hunting
A threat hunter tests a series of hypotheses in the hope of detecting an unknown threat on the network or proving that a given threat does not exist. As a result, it can be very valuable to an organization for detecting current threats on their systems and for providing an accurate estimate of the organization’s current level of cyber risk.
However, the benefits of threat hunting do not end here. In the course of a threat hunt, the hunter defines and refines a method for detecting a specific threat on the network. In the end, even if the result of the hunt was disproving the hypothesis, this detection mechanism can be added to the organization’s cybersecurity toolkit. By automating the tests and analysis, the organization may be able to more rapidly find future threats or even detect and block attacks in progress.
Threat hunting also refines the threat hunter’s knowledge of their network infrastructure and of the potential threats than the organization can face. This knowledge can be invaluable for securing the organization, which is why a security team with threat hunting capabilities can be invaluable for organizations trying to manage their cybersecurity risk posture.