SOC as a Service
Integrate a Managed Security Operations Center (SOCaaS) to rapidly improve security, meet compliance & reduce risk cost effectively.
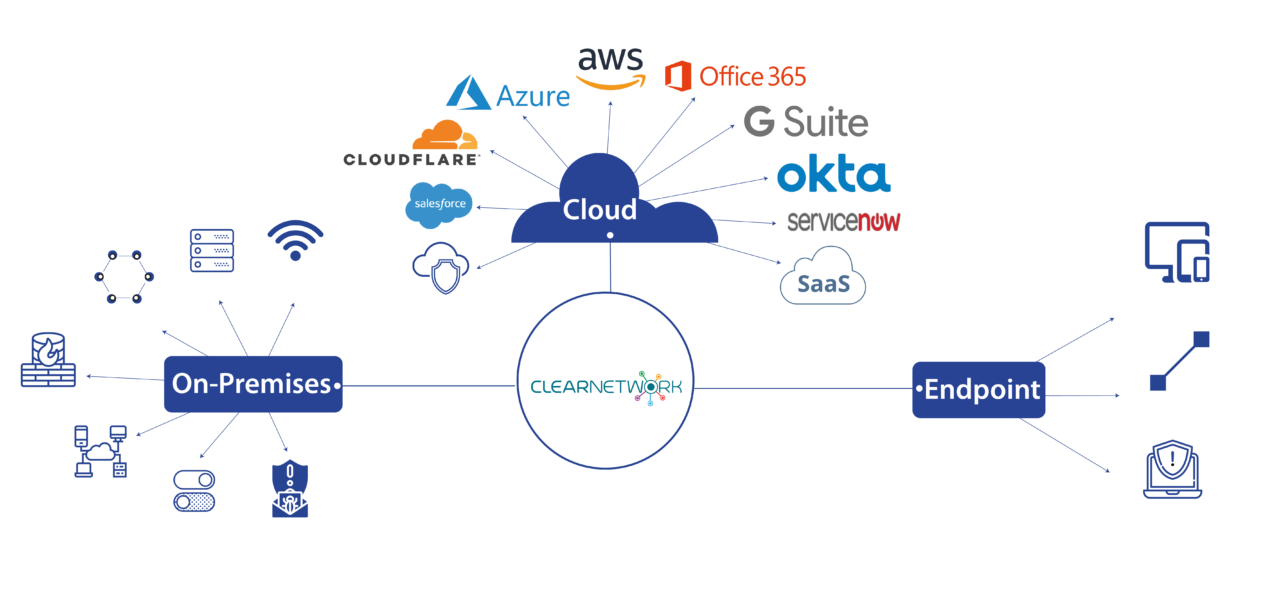
Clearnetwork’s SOC as a Service integrates with your network, cloud, & applications providing 24/7 monitoring with real-time detection, threat intelligence, analysis & reporting from our US based SOC using the best-in-class Alienvault platform. The result is that we detect and respond to threats quickly, & accurately.
MSP or Solutions Provider looking to partner? Ask us about our partner program.
200+
98%
Customer Retention Rate
20+
Years in business
Detect and Respond to Cyberthreats Before they Impact your business with Clearnetwork’s Managed SOC.
24/7 SOC as a Service
Expert security analysts in our US based Security Operations Center (SOC) are assigned to your network and continuously monitor your network, cloud, applications and endpoints for threats. When a threat is detected we immediately reach out to your team to help remediate it. We can even contain threats.
Advanced Compliance Reporting
Having the right technology and expertise to achieve compliance and satisfy upper management can be challenging for organizations of any size. We enable you to be compliant with PCI, HIPAA, NIST and other regulations with our powerful reporting capabilities, we can fully customize reports.
User Behavior Analytics
Users are one of the greatest threats to your network. Our User Behavior Analytics (UBA) capability enables us to identify malicious or compromised users and gives you the insight you need to make informed decisions quickly.
Multiple Threat Intelligence Feeds
We use the latest threat intelligence from multiple feeds to keep your network secure against the latest threats. New threats appear continuously, and threat intel is vital for quickly and accurately identifying indicators of compromise (IOCs).
Threat Hunting & Containment
Our expert security analysts search deep for hidden threats in your infrastructure that threat intelligence has not yet discovered. We can even disable networking on infected devices to stop the spread of an attack.
Endpoint Detection and Response
Lightweight agents on endpoints of your choosing enable our analysts to paint a more comprehensive picture. This gives us the ability to respond with contextual information, conduct File Integrity Monitoring (FIM) and much more.
Clearnetwork has streamlined our detection strategy. Our staff used to spend hours daily looking at logs and trying to filter out false positives. Now with Clearnetwork, they only work with actionable data for validated threats.
Want to get in touch more quickly? Give us a call 800-463-7920 x3

Why Choose Clearnetwork?
Clearnetwork is 100% focused on cybersecurity.