What email threats are common?
The world is a dangerous place for anyone who uses email. There are malicious messages arriving all the time, and many of them are from malevolent people seeking to steal your information and your money. Users must be aware of these email threats and there must be systems in place that can effectively defend against them.
Five specific email threats are and will continue to be extremely prevalent. In this article, we’ll review these forms of attack and look at the best ways to avoid them.
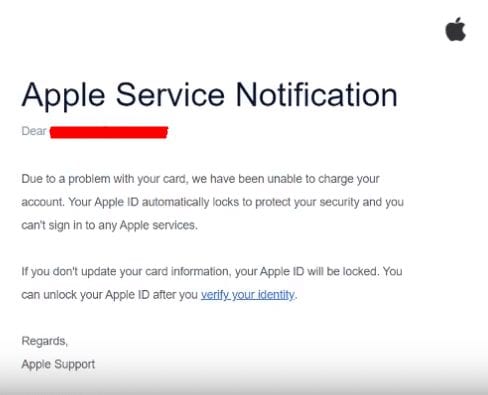
Phishing is simply sending out an email to someone hoping that they will divulge personal information. Spear phishing is a more targeted variant of the threat. In spear phishing, the hacker presents actual information about the target, such as the existence of a bank account or membership in an organization. The hacker might ask for information directly or simply plant a bug in the computer that will dig out information.
Phishing – Phishing is simply sending out an email to someone hoping that they will divulge personal information. Spear phishing is a more targeted variant of the threat. In spear phishing, the hacker presents actual information about the target, such as the existence of a bank account or membership in an organization. The hacker may ask for information directly or include a link to a cloned version of a legitimate trusted source that seeks to get your password.
The most effective way to combat phishing is never to disclose any personal information via email. If you receive an email from, for example, your “bank,” asking you to send them your password information, log directly into the bank’s website to investigate further. (And use the bank’s official URL—do not click on a link in the email!) No reputable bank should ever send emails requesting password changes, if they do you should go on their website directly and call them to verify.
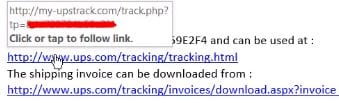
Malicious Links – A malicious link is embedded in an email; it leads to a site that will attack a computer or a network. Often, the attack happens before the person can even click away from the site. This type of attack is most commonly a link sent from a spoofed account—the email address or name appears to be that of a friend or business associate. Often it will contain only the link, or it will say something like, “I found this for you…”
There are two ways to combat malicious links.
The first is to simply never click a link in an email from an unknown source. If someone recommends that you check out a particular website, search for the website and go to it from the outside. If you choose to use the link, hover over it and see the URL behind the words. This will often show in the lower left-hand corner of the screen. If it’s not the link that you’re expecting, don’t click it. If a URL shortener is used, never click the link.
The second is to get an email security service with URL protection. This checks all links to make sure they don’t lead to known malicious sites. Once the service has checked the link, the email is released to the recipient. Our email security service, ContentCatcher, has this feature.
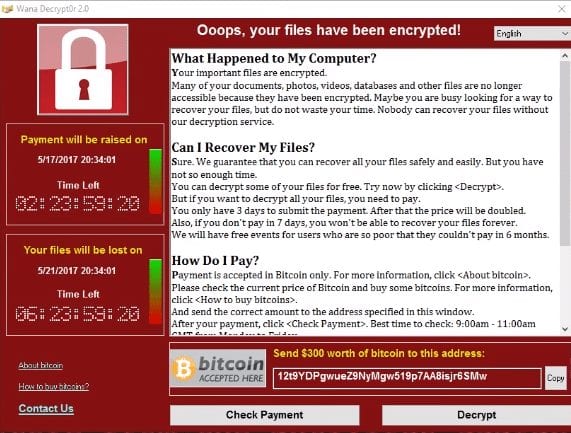
Ransomware – This type of threat has been in the news in recent years and has even been the subject of TV shows. In a ransomware attack, a user opens a piece of software containing a virus that locks up the user’s device and likely propagates throughout the network.
Again, there is a human solution and a technological one. The human solution is to not open emails, links, or attachments that come from unfamiliar sources. If you have any question whether something is legitimate, call the person who sent it. Since most viruses don’t come through the email itself, you will have to take one more step for the ransomware to affect you. The technological solution is to have an email security service that scans all attachments and links as well as next-gen anti-virus like Carbon Black Defense. With these two solutions in place, the chance of a ransomware attack on your network decrease significantly.
Business Email Compromise – most commonly begins in the form of spoofing, spear-phishing and/or malware. These types of attacks most commonly aim to gain fraudulent wire transfers by appearing as a customer or vendor that you commonly do business with.
How to avoid BEC
Think about the habits of your customers and people you do business with, such as the amount of payments, and reasons behind their requests – this alone will help you catch malicious requests
Limit the people within a business who can conduct wire transfers and require approval from others and confirmation from a source at the recipient before any money is sent.
Slow down – if you are still suspicious, don’t send the money, take extra precautions such as rechecking the routing number with your records and confirming with a trusted contact at the recipient that it is correct.
The FBI has a good resource on Business Email Compromise here.
Zero-Day Attacks – In a zero-day attack an attacker uses an unknown threat (yet to be discovered by anti-virus vendors, firewalls, and other systems). Email is the most common form of delivery of these types of attacks through malicious links or attachments. Once someone clicks the link or attachment in the email, the malicious code installs itself and exploits the unknown vulnerability.
The best way to avoid zero-day attacks is to block them at the source, which is email. By having advanced cloud based email security in place that uses system emulation on attachments and dynamically scans URLs, you will eliminate the vast majority early. When one of these threats slips past email, you need to have next-gen antivirus like Carbon Black which watches for the behavior that is taken in real time and does not require rule updates. The main reason zero-day attacks are so successful is that most prevention systems work on statistics and rule updates, and if they’ve never seen something, it won’t get blocked.
Spam – While most spam is benign and just a nuisance, there are forms of spam that carry ransomware, malware and other threats like keyloggers. For example, a friendly email from some car dealer you don’t remember speaking with may contain a malicious link behind the “Check deals” button. These techniques are dangerous because people tend to click first and just assume it is safe. You need to be vigilant, hover over all links in email to see if they look suspicious and have proper email security in place which filters out spam and has URL defense in place to dynamically scan all URLs to look for threats.
How to stay out of trouble
There are two simple ways to stay out of trouble with malicious email. The first is to use an advanced email security service with comprehensive features like URL and attachment protection, ours can be seen here. The other is to teach your staff how to avoid falling victim to malicious emails. Human error is the number one way that these threats get into networks and computers.