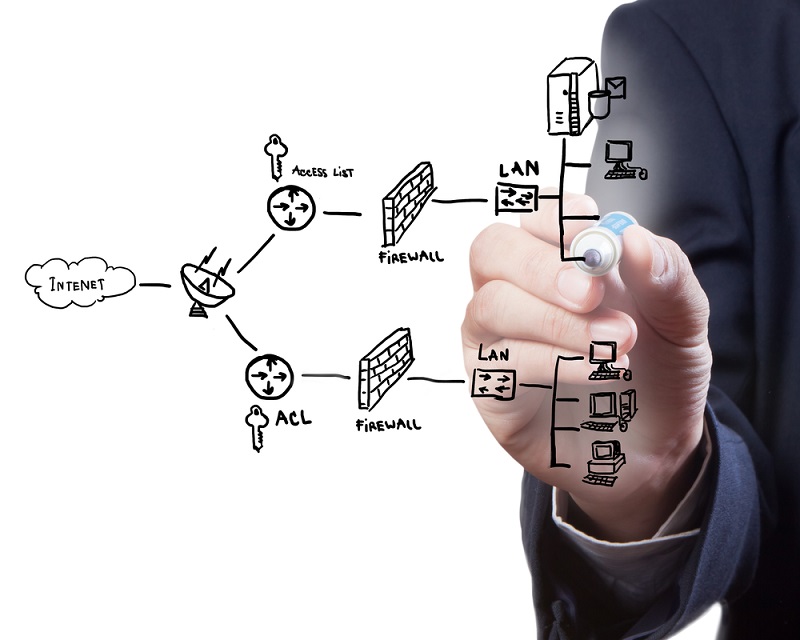
Introduction
Cybersecurity is a serious topic, it needs to be top of mind at businesses of all sizes. Websites are getting hacked, companies are losing money and information, and reputations are being damaged.
This will be more than an overview; it’s designed to be a practical guide to walk you through the different aspects of security that are important for small to medium sized businesses in particular.
Recognizing the need for cybersecurity
There are a few facts that every business owner should know:
- Most small and medium-sized business that get hacked are out of business within a year.
- It can cost over $100,000 to clean up the mess made by a cyber-attack. That doesn’t include potential lawsuits.
- 2017 saw only 29% of the number of attacks than there were in 2016, but the attacks were much more vicious than ever before.
- Increasingly, cybercriminals are attacking smaller businesses, as larger enterprises secure their information better.
- Only 25% of small businesses are well prepared for a cyber-attack.
Not just a problem for big business
There is an attitude of invulnerability among small to medium-sized business owners. Too many small businesses believe they have no information that a cybercriminal would want.
In truth, even a tiny business has a lot of information that bad guys would want:
- Customer data, including addresses and phone numbers
- Purchasing information
- Payroll information
- Customer payment information
- Social security numbers
- Work and personal emails
- Product designs
- Marketing information
- Financial records
- Tax information
Action Step
Do an inventory of your current status:
- What kinds of data does your business keep? Look closely at everything. Every set of data, like phone numbers and social security numbers, needs to be looked at. This includes your company’s data, such as proprietary plans, marketing information, and employee records. This will constitute the list of everything you need to protect.
- How is the data handled and protected? Look at what’s happening to that data as you work with it, throughout your company.
- Data is at its most vulnerable when it’s in motion. Is data being passed over the internet? Is it remaining on a closed internal network or a single computer that’s not connected to the internet?
- What does your network look like? What data is moving on that network? How is it protected?
- Who has access to the data and under what circumstances?
Moving forward, we’ll be talking about each of these issues in greater depth, but for now, do an inventory of where you stand so you can clearly see where you need to go.
Privacy and data security
The need for security is universal. Everyone, whether they’re using a single laptop or a global corporate network, needs to secure all their data and communications.
The legalities of privacy and data security – Around the world, there are laws that govern what data is to be saved, how it’s to be protected, and how the company will report on data losses.
- HIPAA – The Health Insurance Portability and Accessibility Act (HIPAA) is the law that governs how personal health information (PHI) is handled, how it can be accessed, and how that information is stored. The penalties for failing to comply with HIPAA or even an inadvertent data loss are steep.
- Securities – The Securities and Exchange Commission (SEC) has a set of guidelines that governs the uses, storage, and transmission of financial trading data. In many ways, their guidance is very vague, using phrases like “reasonable investor” and “material impact.” This is in contrast to the next set of guidelines, which lists very specific requirements for all organizations.
- GDPR – On 25 May 2018, the European Union (EU)’s General Data Protection Regulation (GDPR) went into effect, strictly governing customer data and rights. This law has become the global standard for how global companies handle data. It’s important to note that even if you have only a few customers in the EU, you are subject to GDPR.
- Employee privacy –
Action Step
Now that you know what the data is…
Once you have a handle on what types of data your company stores and some of the legal requirements concerning its security, it will be helpful to begin tracking where it’s located and how it moves about.
- Look at each piece of data and its current storage point: Is it where it belongs in terms of workflow? Can this data be archived, meaning is it in active use now, or can it simply be put away in case it’s needed?
- Is the data delivered to end-users in the most efficient manner? For example, is data that is used by one facility stored in an entirely separate facility?
- Who has access to the server hardware? Should they have access?
- Is data being exchanged via email? Is that email secure? If your data is often being accessed and transmitted via email, know that the email system is frequently the portion of the transaction that proves to be the weak link. The subject of email security service will be discussed at length later in this book.
Off-site storage – The standard in the cybersecurity industry is off-site storage. This can mean a single location in a data center, or it can be in the cloud.
Data center storage – Data center storage has some significant advantages to maintaining servers on your own property. The people who run the data center have no idea what data you hold, so they are much less likely to steal it or make a mess of it.
The cloud – The cloud most often provides state-of-the-art data security. The companies that run cloud storage sites have as much interest in keeping your data secure as you do. The cloud is able to provide you with amazing levels of encryption and security.
Encryption – Encryption is an old concept that has gotten many upgrades since it first appeared in digital form. Today’s best encryption systems are nearly impossible to break and provide security end-to-end, meaning that only the authorized computers and personnel can crack the code.
Action Step
Creating a privacy policy is the first step to success. A privacy policy defines what information is to be restricted and who will have access to it.
The most important thing to remember about cybersecurity is that humans—the ones with access to your data—are the weakest link. Establish clear policies for your staff in terms of what they should be doing and how they are expected to protect data.
A privacy policy starts with a simple statement that clearly describes what information you will gather from your customers and staff, and how that information is to be handled.
Your privacy policy will spell out precisely how you and your staff will abide by stringent guidelines to protect your brand from public backlash.
The policy should address the following types of data:
- Personally Identifiable Information (PII) – This includes, but is not restricted to, name, business information, address, phone number, banking information, email address, credit card information., taxpayer certification, gender, date of birth, and Social Security Numbers.
- Personal Health Information (PHI) – Sensitive patient information can be very valuable. Not only is it clearly protected by HIPAA, but the loss of this data can be very costly in terms of customer faith. Guarding patient data is always important, but when that information pertains to co-workers, it’s even more imperative to make clear who has access to it. Protecting PHI from future employers and insurers is also very important.
- Customer Information – Whenever a customer places an order, they volunteer more than just their payment information. Their purchase history, billing and shipping addresses, phone numbers, and more are all valuable.
Your privacy policy needs to clearly delineate the following factors:
- Precisely what data your firm collects
- Who will have access to that data
- Under what circumstances those people will have that access
The Better Business Bureau offers an excellent example of a privacy policy.
For an example of a massive and complex privacy policy, Google’s policy is an ever-expanding maze of products and ideas.
Most privacy policies have seen massive updates since April 2018, with the arrival of GDPR. In fact, it’s likely that your inbox has been filled with updates as companies adapt to this new law. It’s worth noting that within hours of the law taking effect, there were lawsuits against Facebook and Google for non-compliance. Larger companies have been given no extra time to comply. Smaller firms are less likely to find themselves under attack in this way. After all, it’s Facebook and Google that are largely impetus behind the law.
A solid privacy policy is the first step to abiding by international law. Remember, complying with international law is wise, since you never know where your customers might be coming from.
Scams and Fraud – There are a number of scams and frauds that cybercriminals perpetrate. These evolve over time, but at their core is the need for someone to fall prey to them. This isn’t the same as a direct attack on your server—we will look more closely at those kinds of attacks in a later section.
Phishing – Phishing is the umbrella term for scams that involve communicating with someone within a company’s sphere and thus gaining access to protected information.
Types of phishing – There are cute names for the major types of phishing. Each is a shorthand for a certain tactic.
- General phishing – This a spray-and-pray type of phishing. A criminal will mass-mail a large number of people in an attempt to entice a few to give them some data that they can use. These attacks are often based on spoofing—the email header or sending address looks like a business or person that the recipient will recognize. While phishing messages often look like FedEx notices or bank updates, they can be based upon any organizations that a person belongs to or individuals whom they know.
- Spear-phishing – Rather than a random, large-scale attack, spear-phishing specifically targets high-value persons and/or organizations. For example, a nation-state will target an employee of a rival government, or an industrial spying group will target someone in a competing firm. Aimed at an individual, these scams are designed to gain access to sensitive information through trust.
- Whaling – Whaling is a form of spear-phishing that goes directly to a top-level executive in a firm. CEOs, CFOs, and board members are the targets in an attempt to get from them specific information that the attacker can use to gain access to nearly everything a company has. This attack will start with social engineering, the perpetrator discovering as much information as possible about the VIP he or she is targeting.
- Cloning – In a clone-phishing scam, the phisher looks for a legitimate email that has already been sent to a target in a company. They will then resend it with a piece of malicious code that then attacks a system, or they will simply change some of the data and get negative information from the target.
All phishing is based on a bit of social engineering, using available data to get “into someone’s mind” and begin manipulating their trust and responses.
The social engineering experiment
We started with an organization that we’ll call the Advanced Global Communications Group. They are having a conference in about five months, so it’s a great time to reach out to them to get information.
We used their membership list to find a member company, AdFuzz (a false name). Now we know what company to target. Then we used connect.data.com to look up people who work for AdFuzz.
There we found Lynne L., the buyer and procurement manager, along with her email address.
Here is an approximation of what a social engineering email might look like:
Subject: Will you be at the AGC Conference?
Dear Lynne,
I found you through the AGC membership list, and I would like to talk to you about supplying our widgets to AdFuzz. I, of course, think ours are the best, and I wanted to show you what we’re doing at the conference in Orlando this August. In fact, if you’re using Johnson Systems’ widgets, ours are nearly identical but 25% less expensive.
If you’re going to be there, let’s set up an appointment. Otherwise, I plan to be near your offices in Cincinnati in September. Perhaps I can see you there instead.
If you can give me your admin assistant’s information, I will reach out to her or him and make an appointment.
I hope to meet you soon, and I look forward to working with you.
Thanks.
John Hopkins
By the time we get a reply, we will know the following:
- How receptive Lynne is to cold emails (We would be able to run other scams.)
- How likely she is to share information (We can dig for more vital info.)
- If she works with Johnson Systems and buys their widgets (We can scam her Accounts Payable department to pay a fake invoice.)
- Her admin assistant’s name and info (We can use it to get sensitive information in Lynne’s name.)
- If she will be in Orlando in August (She is less likely to take calls from the office at that time, so we can run a pressure scam on her staff then.)
All of this will come from a single reply. Social engineering takes time, but it can be very lucrative.
For example, let’s assume that Lynne’s company buys $1 million in widgets from Johnson Systems every year. A single invoice could be worth $100,000. That’s a decent payday if we want to work on dozens of people at once.
The key, however, is knowing that Lynne’s email is Lynne.L@adfuzz.com. Using that information and the names of her admin assistant and the folks in the accounting department, we can get access to other critical email addresses and use them for a forwarding scam, a CEO scam, or a lot more.
Action Step
This is a great time to think about putting together an anti-phishing training program for your staff and a set of corresponding policies.
Since all phishing requires the targeted person to do something, you can reduce the risk by teaching people what to look for, what to do, and what not to do.
Here are some of the things your staff should bear in mind as they look at an email message:
- The sender – Look closely at the sender’s name and how it is written; this is the starting point of getting control of phishing. For example, if you regularly receive email from “Bill Price” and suddenly an email appears that says “William Price,” you have cause to be suspicious.
- The subject line – Attackers often use an urgent subject line that will get people to act without thinking. For example, “Please send us this information today” is designed to get the recipient to respond quickly without looking closely at the message details.
- The body – The body of the email might contain masked URLs, images to click, and more. Look for odd word choices suggesting that the writer is not a native speaker of the language.
- Attachments – Be very suspicious of any email attachments. They may initially seem important or necessary, but they can contain malicious software.
- URLs – Even URLs that look right at a quick glance can be malevolent. For example, without paying close attention to the URLs, it’s easy to confuse www.usbank.com, and www.usbank.co. One will take you to your bank. The other might take you to a site that looks like your bank’s website but is actually designed to steal your login information.
Create a training course that teaches your staff to avoid getting phished and scammed.
Here are the basic concepts to teach:
- Don’t trust the name – Even if a name looks right, it can be wrong. Compare all the elements—the sender’s name, the email address, the reply address, and the URLs—to make sure that everything is as expected. If they have any doubt, they should call the sender or go directly to the company’s website, avoiding the links in the email.
- Tell them nothing – If one receives an email looking for sensitive information, send nothing without directly contacting the sender via another channel to confirm that they sent the email.
- No replies – If someone sends a new message that is “Fwd:” or “Re:” it should be regarded with suspicion. This is one way of creating urgency or making it look like you’re in a conversation already.
- RUSH – Don’t. No legitimate source would try to get you to hurry. For example, your vendors wouldn’t send you an email saying, “Pay this today.” A message that says “Overdue” is much more likely, and even then, one should call to make sure it’s legitimate.
- Check the signature – Very often, a scammer won’t get the signature line correct. They will guess at what’s supposed to be there, or they will alter some of the data to suit their needs, such as changing the phone number to their number.
- Unexpected change – If you get a message something to the effect of “account number for payment has changed,” call the sender. Don’t believe the email. The new number could well be an account in the Cayman Islands or Nigeria, rather than the valid one.
The simplest way to teach people to avoid phishing scams is to call real humans and have real human interactions. This even includes messages from the company’s own management. If an employee receives an email, ostensibly from the CEO, that says, “Please wire $100,000 to this account as a down-payment for services,” he or she should call the CEO directly. No CEO will get angry at a cautious, diligent employee protecting the company’s assets.
There is a simple way to develop and deliver this training: Hire an outside third party that has developed the program and will do the training. It will often come with monitoring services. It might seem like an unnecessary expense, but consider this: the average cyberattack can cost over $100,000 to clean up and is likely to put a small or medium-sized firm out of business within a year.
An email security service is essential. The best of them will scan URLs that are in the emails, hold attachments and scan them thoroughly, and look at senders’ addresses to make sure that they’re legitimate. An email security service is as essential today as antivirus software and a privacy policy. The majority of malware travels via email, and an advanced email security service located in the cloud can intercept problems before they get to your computers.
The cost of hiring someone to do the work is minor compared to those losses.
Network security
The next cybersecurity step for the small to medium-sized business is to secure the network. There are several steps involved here, even if the company’s primary storage site is in the cloud.
Next-generation antivirus –
Traditional antivirus software awaits malware updates from the designer, and then it will simply look for and block those pieces of malicious code.
Next-gen antivirus does this, as well, but then it also learns from attacks it’s never seen before.
Here’s an explanation borrowed from the Carbon Black website that defines what this technology is all about:
“NGAV does four critical things to protect businesses:
1 – Prevents commodity malware better than traditional AV
2 – Prevents unknown malware and sophisticated attacks by evaluating the context of an entire attack, resulting in better prevention. (Traditional AV does not.)
3 – Provides visibility and context to get to the root cause of a cyber-attack and provide further attack context and insight (Traditional AV does not.)
4 – Remediates attacks (Traditional AV simply stops mass malware.)
Additionally, NGAV is easy to deploy and easy to administer from the cloud.” – Carbon Black website, accessed 5/27/2018
The biggest change between traditional antivirus and next-gen is that the latter learns while the system is under attack, and it even learns from the malware that it detects and blocks before it can do any damage.
Because next-gen software, like Carbon Black, resides in the cloud, it’s updated instantly. With the speed that malicious software can travel the world, this speed can mean the difference between getting infected with ransomware, for example, and avoiding it.
Next Gen Firewall –
An advanced firewall like a Palo Alto is a great first line of defense in stopping all types of cybersecurity threats.
Utilize an MSSP for Managed Security-
The MSSP (Managed Security Services Provider) you choose to work with is a major factor in the ultimate security of your network. An MSSP looks for the threats that your prevention systems (like your firewall, and anti-virus) miss. Most of the time these missed threats are the ones that do the most damage since they can remain on your network for months before ever being discovered if you don’t have an MSSP hunting for threats. Your MSSP will be your security adviser, in a way, your virtual CISO.
Clearnetwork is an MSSP and has specialized in security since 1996. Give us a call at 800-463-7920 x3 or sales@clearnetwork.com and check out our services in detail here
Backups – Backing up your entire system is at the heart of successfully keeping it working well. If your server is infected, you can restore it to an earlier version that was working well. On some systems, this is an automated function.
Utilize an MSP for Network Monitoring –
This is like having your own IT team to keep the network and computers up to date and running smoothly.
- Server Health
- Patch Installation
- Anti-virus installation and updates
- System backups
Action Step
A network security survey is the next logical step:
- Are you constantly backing up your servers’ data to a secure location(s)?
- Is your antivirus software a next-gen program? Is it cloud-based?
- Do you have an email security service in place?
- Have you looked at the advantages of migrating to the cloud and securing your company’s information off-site?
- Do you have monitoring, not just for cyber-attacks, but also for network health? Who will you call if your network is attacked? Do you have people who can fix the problem for you?
The answers to these questions can be complex. If you are not the Chief Technology Officer, you might need a bit of advice. There are lots of options, because different firms have different needs.
If you don’t feel 100% confident in making these types of decisions, now is a good time to get a consultant, particularly a network security consultant. They can discuss your options with you and help you decide the best path to take.
Website security
Your website is your face to the world. Even if you don’t sell through your website, it’s important that you have everything in order so your customers can visit your site safely and with the knowledge that everyone’s data is secure.
Here are some of the basics that you should look at to keep your site safe:
SSL – Secure Sockets Layer (SSL) is the most basic security that your website should have. This is an encryption system that encrypts data from the server to the browser. When you’re on a website that is secured, it will show a lock in the address bar, and the site is accessed via “https:”
At this point, every website in the world should have an SSL certification. Without it, Google will simply push it down. If you use Chrome, Firefox, or Edge browsers, you are likely to get a security notification. Most people will go back instead of proceeding. In other words, without an SSL certificate on your website, you’re likely losing visitors and customers.
You can get an SSL from your host or just about anywhere else. It acts as an overlay on your website. There are different strengths of SSL certificates, from the most basic, where you don’t take any information from anyone, to ones that are military-grade. The more information your visitors put into your site, the more secure your site needs to be.
Online shops – If you’re running an ecommerce site, you need to be extra secure. You’re not only collecting email addresses but also likely credit card or other payment information.
Most ecommerce sites will opt to use a service like Shopify or WooCommerce. These are storefront templates, and they also provide the complete payment system, hosted on their servers, not on yours. This can remove that data responsibility from you and allow a larger firm to handle it.
Remember that with GDPR in effect, the rules regarding what data can be kept, where, for how long, and how it’s to be handled are all much stricter than they were just a few months ago. Let someone else handle this very important data so you don’t have to hire a Chief Data Manager.
Medical websites – As mentioned above, any Personal Health Information (PHI) needs to be strictly protected. This applies to any website that accepts health data.
Doctors’ sites, insurance sites, and more all require PHI to be entered.
Security on these sites needs to be even stricter than on others. This health data can be used by criminals for some pretty ugly things. HIPAA laws are very strict and provide for huge fines and penalties for non-compliance.
Covering the basics
Most websites offer some variation on “enter your email address and information.” This data, while seemingly innocuous, is extremely valuable. If you can hack someone’s email, you have access to their whole life. In some case, an email and a name are all that are required to place orders for products and start an expensive subscription service.
Email addresses, names, and phone numbers are all relatively easy to find, but, as a business owner, you need to protect them.
Not only does the law require that you keep this information secure, but this is also some of your best marketing data. You don’t want to allow competitors access to it. You may also find yourself unable to collect more data if the world knows that you don’t protect it.
Membership information
Using member information is about social engineering. Most membership organizations want the world to see their membership lists. Those lists are their life-blood.
Members want to be seen as being members, because it lends credibility.
This is all well and good, but it’s also an opportunity for some malevolent social engineering and scams. Please refer to the earlier phishing experiment to see how all of this data can be used to make a criminal rich.
Email Security
Email is the biggest hole in your security, period. The weakest link in cybersecurity is people. They can be scammed, impersonated, and even blackmailed into doing things that they shouldn’t.
People are how the bad guys get in. Like children who open the door for a burglar, people are the most typical way that cyber attackers get in. They are able to gain access through any of the doors that we’ve talked about—whaling, attachments, bogus URLs, and much, much more.
Imagine it like this: You have a fortress, like Fort Knox, but every millisecond, another letter carrier, UPS delivery person, truck, car, and FedEx person shows up, and each carries a package that you have to check in almost no time.
Training and awareness are at the heart of an email security service. No lock in the world is effective if the people in the house leave the window open. As we mentioned earlier, a comprehensive and ongoing email security service training program is the most important element of cybersecurity success.
A training program can be developed in-house, or you can get an outside firm to come in and train your staff. The biggest advantage of using a third party is that cyber-attacks are always evolving, and an outside firm can stay current. They can retrain your staff to spot the latest trends.
Email security is essential.
There are several options here.
- Public, cloud-based – This is the one that we most frequently recommend. These programs catch your emails while they are still in transit on cloud servers around the world. There’s no equipment to install or maintain, and they can work with any network configuration. Simply change your MX record and sync with your active directory, and it’s all set up. The two biggest advantages are 1) the emails are handled before they ever get to your network, and 2) this type of system is updated hundreds of times a day in real time.
- On-premise hardware – Depending on the configuration of your network, you can install an email security system that catches your emails and monitors them. These systems get updates on the latest threats via a subscription service, like a firewall or a traditional antivirus. This might be great for companies that want everything on-site, but they do have the disadvantage of not updating in real time.
- Hybrid – A hybridized system might use a cloud-based filter to get rid of the really ugly stuff. Then an on-premise device can filter through the layers of minutiae to make sure that everything is secure.
If you’re not sure, the cloud-based is simplest to execute. It draws on public information to stay up to date on all the threats, and it can be set up in minutes.
Check out our Guide on choosing Email Security
Understanding business versus personal email
One of the issues confronting most firms is the use of personal email on company computers. Many people will check their mail at their workstation, not realizing that their personal email can infect the company’s network.
Your company policy should address this concern:
- Prohibit checking personal email on company workstations.
- Insist that all personal email is checked on mobile devices.
People will check their email, Facebook, and more, regardless of what policies you put in place, but if most of them abide by the request to use mobile devices to do so, you’re in better stead than before.
Outgoing email is also a problem
Although you want to trust your employees, you need to monitor outgoing emails as well.
A complete email monitoring system will review outgoing emails for sensitive data. PPI and PHI are often attached to emails. Usually when this happens, it’s not done with malice but simple ignorance. Someone thinks that they’re sending information to an authorized person, but in reality, that information is never supposed to leave your facility.
Included in the email monitoring will be reports that will tell you who tried to send restricted data and to whom. This provides an opportunity for retraining.
Mobile devices
Mobile devices are ubiquitous, and users rely on them for nearly everything. From checking email to knowing the temperature outside, everyone constantly looks at their phones.
Some companies have attempted to outlaw them entirely, but that’s unlikely to work. People want to have access to their lives even if they’re at work, so they’re going to keep their phones with them.
In reality, allowing phones to simply be a part of people’s lives and work will cause less disruption than banning them. In a lot of places, especially retail, personal phones are one of the ways that employees serve customers.
Policies
Creating policies that are mobile-friendly and that protect your company’s servers and data will save a lot of time and hassle.
The first policy is that if your staff is going to bring phones to work with them, they should use their personal phones only on personal time. If they use them for business purposes, that’s fine, but they need to be respectful of work time.
- Offer free antivirus protection for everyone’s mobile devices.
- Allow personal devices to be used only on a separate Wi-Fi network from the one that the company’s network uses.
- Make sure everyone understands that the same policies that apply to their company devices also apply to their personal phone.
- Establish a policy that prohibits video streaming. This may appear excessive, but you need to ensure that your bandwidth is available for work.
It might seem an unnecessary expense, but putting in a second Wi-Fi network will keep your systems from getting infected and, let’s be honest, there is no way that you’re going to stop employees from checking their personal email.
Action Step
Policy development and management
It’s now time to look at creating a comprehensive policy guide based on the decisions you’ve made so far.
Comprehensive policy guide
This is only a basic outline of your policy guide, but it’s a place to start.
- Establish roles and responsibilities – Establish clear roles and responsibilities where your cybersecurity is concerned. This will include, but is not limited to, making policy, training staff, maintaining software and hardware, incident response, incident coordination, debriefing, and discipline. Depending on the size of your firm, there might ten people or a thousand in this section. These roles are title-based, not “call John if we’re attacked.” Several laminated master copies can assign a person to each role, including name, phone numbers, email, etc. That list will need to be checked monthly, but it will ensure that everyone’s contact info is in one place.
- Define employee internet usage – This will be the section where you talk about internet searches, social media, and more. This should include mobile devices and Wi-Fi usage. You should define penalties and talk about what training employees should have.
- Whom to call – “Who you gonna call?” is the most important question that your manual should define. In fact, consider putting it on the cover. The plan should have a single point of contact in the event of a suspected cyber-attack. That point of contact should be someone empowered to activate the response and lead the recovery. Make sure that your information is available to everyone, 24 hours a day. That point of contact needs to be available to the overnight watchman, the administrative assistant,
- Response plan – In subsequent sections, we will look at response plans in greater depth, but your response plan should at least be outlined in this policies and procedures manual. If your response plan is large, you should include information as to where staff can find that plan.
- FAQs – Many people will never take the time to read the manual completely. Let them know right in the front of the book that that they should at least read the Frequently Asked Questions. Cover the highlights, the contacts, and make sure that each question is linked to a section of the policy manual.
- Online and offline – While it’s tempting to distribute this manual solely by electronic means, don’t. A cyber-attack can compromise your people’s access to the internet, to your files, and therefore to the digital form of the manual. Have it printed and placed in central locations, like lunchrooms and near entrances.
This policy manual will need to be revisited at least once a year. Roles will change. The data you keep will change. The company’s needs will change. Make sure that you’re keeping this policy as current as your hardware and software.
Action Step
Even after all of your careful planning, after you put in place all of the antivirus protection that you can, you might still find yourself the victim of a loss, theft, or attack.
This is the part where you need a Plan for Data Loss or Theft. We will look at this concept in greater depth further along, but these are the core steps that you need to take.
While this is not a comprehensive guide, here is the basic outline of a plan against data loss:
- Have a control plan – If an active attack is recognized, you need a plan for shutting down your entire system. This might require disconnecting every workstation, shutting down the servers, and then bringing everything back up in safe mode.
-
- Once you’ve been able to shut down, you can restart in safe mode. This is a mode that allows you to clean up with only critical programs running.
- The most likely scenario is that you will need to use an anti-malware or antivirus program, freshly loaded onto the system, to clean it up. If you have a third-party contractor that’s overseeing your system, they can do this remotely.
- The anti-malware program will scrub all your computers and servers, looking for the bad code, which it will quarantine and delete.
- The most likely next step will be to restore the system to a backup point before the arrival of the malicious code. This is where those consistent backups are vital.
- Locate the point of entry
-
- This will likely require a technical team that can look at the logs for every workstation and server to determine when this malicious code arrived. Knowing the point of entry will allow you take actions to prevent further intrusions.
- Retraining, counseling, and/or disciplinary action may be required if the point of entry was an employee’s actions.
- New software or hardware solutions may be necessary if the attack came in through those points.
The Online Trust Alliance (OTA) has put together an excellent Cyber Incident & Breach Readiness Guide. It can act as a handbook to each step of this complex process.
This is another of those points were having a third-party contractor can change everything. They will have a team ready in case of an incident and, like first responders, they can oversee the entire process.
Employees
One more time, the biggest threat to your cybersecurity is your employees. They are human and can make mistakes or bad choices.
Willfully negligent – Some employees will simply ignore what they are asked to do. One way to avoid this is to explain the reason behind everything that you train them to do.
Simply negligent – If your people are taught to be vigilant and they are paying attention, negligence is unlikely. Nonetheless, many of the worst cases of data loss in history have been simple negligence. A laptop forgotten in a cab or an email sent to the wrong person, and thousands of pieces of data gone with malice.
Need to know – The military compartmentalizes information on a need-to-know basis. It is a good idea to do the same with your company’s data. For example, the CEO doesn’t need to know the passwords for the banking system. The CFO doesn’t need to know the individual customers’ email addresses. Line employees in most situations don’t need access to any historical data.
Break data into different pieces and grant access only to those team members who need it.
Firing versus quitting
No employee who has access to important data should be allowed to “work out their two weeks.” It’s important to note that the vast majority of employees will never do anything to harm their current employer, but there are those who will. Recently, a Twitter employee deleted President Donald Trump’s account. It was his last day, and he was “just seeing if I can do it.” No employee on his last day should have access to your restricted data.
If an employee submits their two weeks’ notice, pay them for the two weeks and let them go that day. This eliminates the temptation to steal data or even “just see if I could” types of activity. It’s likely to cost far more in the end if a departing employee decides to steal a ton of data from you or shut down your systems.
Also, have someone review their last month’s work to make sure that there wasn’t anything done incorrectly or maliciously. Again, it’s unlikely, but you don’t want to find out six months later that they deleted a week’s worth of data.
Review data access policies regularly
Make sure that your data policies are under constant review. Each time there is a new form of data gathered, a major change in business practices, or even a quarter has gone by, have a team review the policies to make sure that they are all still applicable, comprehensive, and sound.
Training, training, training
As you have already surmised, constant training is needed. Every employee needs to be retrained at least once per year, if not more often. It wouldn’t be out of the question to have monthly refresher courses, even if those courses include things like updated sexual harassment policy and emergency procedures.
Keeping cybersecurity in the front of everyone’s minds is the best way to make that security effective. Repetition creates vigilance.
Facility security
One area that is often overlooked, particularly in smaller firms, is facility security. Let’s say your server is in a small closet. You might not think of it as being as important as an Amazon data center, but to your company, it is.
- Lock down servers – All servers need to be locked down at all times. Not only should your servers be behind a locked door, but putting them into a locked case can also be a good idea. The server room should only be unlocked by the right personnel.
- Eyes-only access info – There will be things like the operating system codes that, to borrow a phrase from the military, should be “eyes only.” This means that the servers’ access passwords should only be seen by those people who need and will use them to do their jobs. The building maintenance personnel should never need to go into the room to clean or do repairs. The CEO, who likely has no idea what to do with the server, doesn’t need it. Treating the most vital passwords and access information as “eyes only” is the best way to keep them from getting into the wrong hands.
- 24/7 monitoring – 24-hour monitoring is an excellent step toward making sure that your servers are online. The combination of machines and humans that can see what your server is doing at any given time and respond to it will keep a potential incident from becoming a real incident. This is again an area where most companies, even large ones, can benefit from an outside contractor that specializes in server monitoring.
- Cameras and other security measures – Putting a camera in a room where nothing ever moves might seem like a waste, but it’s a simple solution to a potentially huge problem. Ask your security company to install cameras and motion detectors that will set off alarms if they sense movement. That way, you know that your servers are at least as well protected as your hallways.
Action Step
Operational security
This is a deeper dive into your data and information than we have done previously. This is more of a strategic move than a simple defensive move. Here’s how to put together an operational security assessment.
- Identify critical information – In this case, we’re not only talking about the data on your servers but also the information needed to access them. For example, passwords, door codes, and keys; even the location of the servers themselves are all bits of data that you should consider sensitive. If you are running a business with quite a few employees, not everyone needs to know that the servers are in the last room on the right in the basement.
- Assess threats – Not all threats, in this case, are cyber-attacks. Things like flooding, lightning strikes, and earthquakes are also threats to your cybersecurity. You should work to assess all of these threats and how they will be handled. Your threat assessment should include, for example, off-site storage locations. The HIPAA law requires that all correspondence is encrypted and archived in case it’s ever needed. These archives are often stored off-site on third-party servers. While you don’t need to do a complete threat assessment of those locations, they should be identified and recognized as valuable assets.
- Assess vulnerabilities – Weaknesses, like thin doors or unsecured data lines, fall under vulnerabilities. Other vulnerabilities might include the ability of someone to download all the sensitive data, even if they need it. When the Department of Defense lost the information of hundreds of thousands of military personnel, it was on a laptop in the front seat of a car. The person was supposed to have that data, but it was not secured when they lost it. That is a vulnerability that you should look for: the portability of your data.
- Assess risk – A thorough risk analysis might require the input of outside security experts. A digital risk assessment expert might tell you that you don’t need to worry too much about physically securing your location if it’s on a top-secret military base but that your data is vulnerable to an earthquake.
- Respond to assessments based on data acquired – Finally, you need to take action to secure your company’s data. Each step of the operational security study will show you what needs to be handled and likely how to handle it. This is not something that should wait. Data is worth more than gold, so keeping it secure is vital.
Payment cards
A note on payment cards, customers’ credit cards, and another important piece of data—your company credit cards.
Customer card data security
A customer’s credit or debit card is often their lifeline. If it’s compromised, they will never forget who put them in jeopardy. Here are a few rules for keeping your customers’ information safe.
- Enlist an outside company – The easiest way to handle everything is to enlist a third party to handle your credit processing. Once the card is swiped, and it hasn’t left your customer’s hand, the third party will encrypt everything, give you the right tracking codes, and make sure that payment is made to you. This way, your company, whether you sell hotel rooms or horses, is never in actual control of the customer’s credit card information.
- Look at what you need – Look at the information that you do need and make sure that you’re being supplied only that data. Date, time, customer name, credit card type, and amount are usually all that you need.
- Create encrypted, searchable files with access records – In all likelihood, your credit card processor will give you access to the data that you need so that you can reconcile your books and help customers if they need it. Make sure this data is encrypted on your computers and server so that it can’t be used to access customer data. Imagine you’re Jane, and you get a call from John’s Fish Shack about that $25 credit card charge. How hard do you think it will be for a criminal to get Jane to read her card number over the phone?
- Restricting access – Like everything else in the data world, access to this data needs to be restricted to those people who really need it. This type of information is too easy to use incorrectly and can cause a lot of problems—both financial and public relations—if it gets into the wrong hands.
Action Step
Incident response and reporting planning
If you’ve done everything in this manual, you are unlikely to have an incident. But just like a fire or a zombie apocalypse, you need a plan if it does happen. Your incident response plan can be the thing that makes the difference if you are attacked.
Type of incident
The first thing to note is the type of attack:
- Physical – If someone has entered your server rooms and physically taken data or hardware, you will need to be prepared for a crime scene in your building.
- Network and system security – An online attack can be hard to trace, but knowing that the problem started from the outside, without the actions of anyone inside, can make all the difference.
- Data breach – A data breach that started with a phishing scam or intentional act by an employee will need to be treated very differently from other types of issues.
Whom to call
One of the first things that happens in these incidents is that the people in the middle, often the people who see problems first, have no idea whom to contact.
Give staff emergency contact details – This should be part of your training, but even placing posters throughout the offices and building that say, “In case of a suspected cyber incident, call…” will make the response that much faster. Notice it says suspected. Don’t make a line employee decide if it’s real or not. A false alarm might take a few minutes to clear, but if the employee hesitates for those minutes, a minor inconvenience can become a huge problem.
Notify law enforcement – While many local police departments don’t have a full-scale cybercrime unit, state and federal law enforcement do. In the case of things like the WannaCry ransomware, the FBI was able to help slow the progress by knowing where it was and what it was doing. Like a physical disease, letting the authorities know ASAP lets them help you stop the spread and might even give you a solution.
Work as a team without blame – Even if it’s clear that single employee’s negligence caused the problem, now is not the time to assign blame or exact punishment. You need to understand what they saw, what they did, and what their computer did in the seconds before and after the attack happened. Stay friendly and supportive. Get the data you need and look to make changes later.
Start recovery
The next step is to start the recovery. If you have an IT team, they will handle much of this, but if you’re your own tech team or leading the way, here are the most likely steps that you need to take.
- Shut down and disconnect – Shut everything down and disconnect everything. The goal is to isolate the malicious software as quickly as possible. By disconnecting the server from all of the workstations, you prevent the computers from replicating and spreading the virus.
- Scrub network – Using the right antivirus or anti-malware software, you will need to scrub your network. This might mean working with every workstation separately, starting it in safe mode and using an external drive with anti-malware software to clean everything.
- Restore to an earlier date – Using the most recent backup before the malicious software arrived, reset your system. This is why daily or even twice-daily backup is important. You want to be as close to the present moment as possible.
Test often – Just like fire drills, test this recovery plan often. Make sure that everyone knows what they are to do, whom they are to call, and that they will act quickly once the word gets out.
Review plan monthly – It’s important to review this plan monthly. Look for people who might have left or systems that might have changed. Often, when an incident plan falls apart, it’s because one person left, and no one knows who her replacement is.
Debriefing
There needs to be a debriefing session after every incident, no matter how minor. This applies to a massive ransomware attack or a data stick left in the lunchroom.
Bring all parties together – This will include the person who might have caused the compromise, the people who responded, and the people in charge.
Discuss what happened – Review in an unbiased and logical way what happened and how the problem was discovered. If it was a virus entering your system, how did it get in? If it was an outside attack, where did it come from?
How you recovered – Look at how your team recovered. Where there any breakdowns or areas that went really well? Was the response time as expected? Was everyone where they needed to be?
What to do differently – What changes can be made to the plan and the team to make everything better next time? Often the changes are subtle, but the best way to improve is to look at the problems this time.
Don’t punish unless gross negligence is proven – One of the keys to success with a response to a cyber-attack is early response. If people feel that they will be punished unjustly, they won’t speak up quickly, and you might lose precious time. Don’t punish anyone unless they acted in a malicious manner or they simply acted stupidly.
The benefits of the cloud
The cloud is in many ways a better solution than warehousing data on your own server.
By having the cloud act as your server, you need only worry about the security of your individual terminals, not the servers. If a single cloud server is hit by an earthquake or a cyber-attack, it’s far more likely that there is a mirrored image of your data on another, unaffected server. That means that you won’t need to do a reset to an earlier data set.
The companies that run the largest cloud services, like Amazon, Facebook, Google, and Microsoft, all have enormous vested interest in maintaining security, so you’re virtually guaranteed that it will be safe.
A few years ago, an iCloud “hack”—which seemed to have been someone getting onto Apple’s servers and stealing nude photos of female celebrities—turned out to be individual password hacks. The attacker simply found each account and hacked their passwords to steal their data. In other words, it was not a failure of iCloud security.
Summary
This guide was designed to help you create policies and procedures that will keep your company out of trouble in the event of a cyber-attack or data loss. It’s comprehensive (and even a bit repetitive) to ensure that the most important points are clear.
Going it alone versus hiring professionals – If you’re a one- or three-person operation, you might not need to take every step, but you should look at your digital responses and express your concerns to your co-workers. If your company is 100 or 1,000 people, you should consider turning this all over to outside professionals. Even if you have an IT department, they are not necessarily digital security experts. Creating a policy manual, training staff, and monitoring your servers 24 hours a day is likely to be more than they can handle.
Cost of a digital insurance policy
Earlier we stated that it costs about $100,000 for a small company to recover from a data breach. Insurance companies have begun insuring firms for data breaches, including recovery, liability, and fines. According to industry sources, the cost of the policies can range from $5,000 to $50,000 a year for $1 million to $10 million in coverage. This might be worth considering if your firm handles data that is sensitive or financial in nature. You might also be covered for some damages through your payment card processor. It’s worth exploring this type of protection.
The necessity of a plan
Throughout this guide, we have talked about the importance of making a plan. Once more, we want to stress that for many firms, the issue of a cyber-attack or data loss is not a matter of if but a matter of when.
Create a plan. Be ready. Keep your company safe from data breaches.
Resources
In their Cyber Security Planning Guide, the Federal Communications Commission (FCC) provides an excellent list of publicly available resources that can help you make informed decisions and learn more on the subject.
We’ve taken the liberty of copying that list here for you:
Cyber Security and Privacy Protection
- Center for Internet Security (CIS);
- Free online security check-ups;
- National Cyber Security Alliance for Small Business Home Users:
- OnGuard Online:
- SANS (SysAdmin, Audit, Network, Security) Institute’s Most Critical Internet Security Vulnerabilities:
- Security Tips from Securing our eCity:
- Small Business Solutions form StopBadware:
- The Open Web Application Security Project:
Cyber Security Threat Centers
- Cyber Safety Links for High School Students
http://blackboard.aacps.org/portal/lor/obj/mods/4students/HSCybrSfty/addlinks.pdf
- McAfee Security Solutions for Small Business:
http://shop.mcafee.com/Default.aspx?site=us&pid=HOME&CID=MFE-MHP001
- Symantec Security Solutions for Small Business:
Training and Exercises
- Free training materials, security configuration guides from Internet Security Alliance:
- Free DOD user training:
http://iase.disa.mil/eta/Pages/online-catalog.aspx
- NIH Free Online User Training (non DOD version):
http://irtsectraining.nih.gov/publicUser.aspx
Government Resources
- Department of Homeland Security (DHS)’s National Strategy to Secure Cyberspace:
http://www.dhs.gov/national-strategy-secure-cyberspace
- DHS testimony before the House on Committee on Homeland Security Subcommittee on Cybersecurity,
Infrastructure Protection, and Security Technologies:
http://www.dhs.gov/ynews/testimony/testimony_1300283858976.shtm
- FCC Cyber Security Encyclopedia Page
http://www.fcc.gov/cyberforsmallbiz
- FCC Public Safety and Homeland Security Bureau Clearinghouse:
http://publicsafety.fcc.gov/pshs/clearinghouse/index.htm
- FCC Public Safety and Homeland Security Bureau Guidelines for Emergency Planning: http://transition.fcc.gov/pshs/emergency-information/guidelines/
- FCC Ten Cybersecurity Tips for Small Businesses
http://hraunfoss.fcc.gov/edocs_public/attachmatch/DOC-306595A1.pdf
- Federal Trade Commission Guide for Business
http://www.ftc.gov/bcp/edu/microsites/infosecurity/
- Federal Trade Commission – Identity Theft Information:
http://www.onguardonline.gov/topics/computer-security.aspx
- Federal Trade Commission’s Interactive Tutorial:
- National Institute of Standards and Technology (NIST)’s Computer Security Resource Center:
- NIST briefing on Cybersecurity for Small Businesses:
http://csrc.nist.gov/groups/SMA/sbc/documents/sbc_workshop_presentation_2015_ver1.pdf
- NIST Guide to Selecting Information Technology Security Products:
http://csrc.nist.gov/publications/nistpubs/800-36/NIST-SP800-36.pdf
- NIST’s Risk Management Guide for Information Technology Systems:
www.csrc.nist.gov/publications/nistpubs/800-30/sp800-30.pdf
- NIST Small Business Corner – A link to the NIST-SBA-FBI Small Business Information Security outreach pages :
http://csrc.nist.gov/groups/SMA/sbc/index.html
- NIST Small Business Information Security:
http://nvlpubs.nist.gov/nistpubs/ir/2016/NIST.IR.7621r1.pdf
- SBA, NIST and FBI partnership on Cybersecurity for small businesses:
http://csrc.nist.gov/groups/SMA/sbc/overview.html
- United States Computer Emergency Readiness Team (US-CERT):
- U.S. Department of Homeland Security Cyber Security Resources:
Publications
- Cloud Security Alliance
https://cloudsecurityalliance.org/csaguide.pdf
- Computer Security Resource Center, National Institute of Standards and Technology:
http://csrc.nist.gov/groups/SMA/sbc/library.html
- Microsoft Small Business Guide:
http://download.microsoft.com/download/3/a/2/3a208c3c-f355-43ce-bab4-890db267899b/
Security_Guide_for_Small_Business.pdf
- Protecting Your Small Business, Entrepreneur Magazine:
http://www.entrepreneur.com/magazine/entrepreneur/2010/june/206656.html
- Small business Information Security: The Fundamentals, National Institute of Standards and Technology:
http://csrc.nist.gov/publications/nistir/ir7621/nistir-7621.pdf